OpenMetadata Vulnerability Exploit – Cryptomining Attacks on Kubernetes – In a concerning development, cybersecurity experts have uncovered an ongoing campaign where threat actors are exploiting critical vulnerabilities in the OpenMetadata platform to launch cryptomining attacks on Kubernetes workloads. This sophisticated operation highlights the growing risks associated with open-source software in containerized environments.
OpenMetadata, a widely-used open-source metadata management tool, has become the latest target for hackers seeking to capitalize on its flaws. These vulnerabilities, including CVE-2024-28847, CVE-2024-28848, CVE-2024-28253, CVE-2024-28254, and CVE-2024-28255, were initially disclosed and patched in versions 1.2.4 and 1.3.1 on March 15. However, despite the patches being available, threat actors have been actively exploiting them since early April, emphasizing the importance of timely updates and patch management.
The attack methodology of OpenMetadata Vulnerability employed by these hackers is alarming in its sophistication. First, they identify vulnerable versions of OpenMetadata running on internet-exposed Kubernetes workloads. Leveraging the disclosed vulnerabilities, they gain unauthorized access to the containers, ultimately achieving remote code execution.
Once inside, the attackers conduct reconnaissance to assess the compromised environment thoroughly. They collect information about the network, hardware configuration, and operating system version to tailor their subsequent actions. Interestingly, they utilize ping requests to domains associated with Interactsh, a tool for detecting out-of-band interactions, to validate network connectivity without raising suspicion.
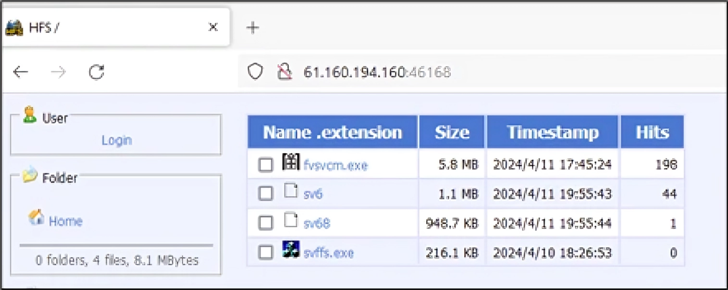
Upon confirming their access, the hackers proceed to download cryptomining malware payloads from a remote server, often located in China. These payloads, available for both Linux and Windows platforms, are then deployed within the compromised containers, initiating cryptocurrency mining operations.
To maintain persistence and control over the hijacked Kubernetes applications, the attackers employ various techniques. They remove initial payloads, establish reverse shell connections using tools like Netcat, and set up cronjobs to execute malicious code at regular intervals.
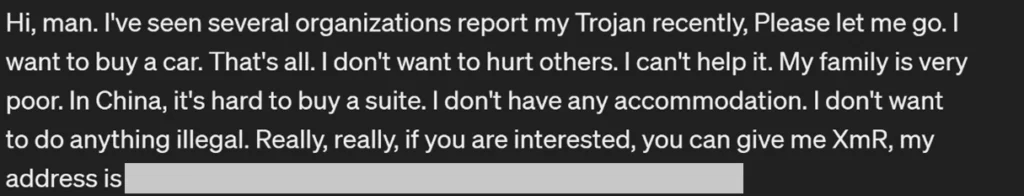
Notably, the attackers leave behind a distinctive calling card—an appeal for Monero cryptocurrency donations, purportedly to fund personal expenses such as purchasing a car or a “suite” in China. This tactic adds a peculiar twist to an otherwise malicious operation.
Security experts urge administrators to take immediate action to mitigate the risk posed by these attacks. They recommend changing default credentials, ensuring that OpenMetadata applications are promptly patched against known vulnerabilities, and maintaining vigilant monitoring of Kubernetes environments.
To maintain vigilant monitoring of Kubernetes environments, administrators are advised to take proactive measures. This includes promptly changing default credentials, ensuring that OpenMetadata applications are updated against known vulnerabilities, and utilizing the following command to get a list of all OpenMetadata workloads running in their Kubernetes environment:
kubectl get pods --all-namespaces -o=jsonpath='{range .items[*]}{.spec.containers[*].image}{"\n"}{end}' | grep 'openmetadata'
By running this command, administrators can efficiently identify any instances of OpenMetadata running within their Kubernetes clusters, allowing for timely assessment and response to potential security threats. This proactive approach is crucial in safeguarding digital assets against emerging cyber threats.
This incident underscores the critical importance of maintaining robust cybersecurity practices, including timely patching and proactive threat detection, in containerized environments. As the cybersecurity landscape continues to evolve, organizations must remain vigilant to safeguard their digital assets against emerging threats.