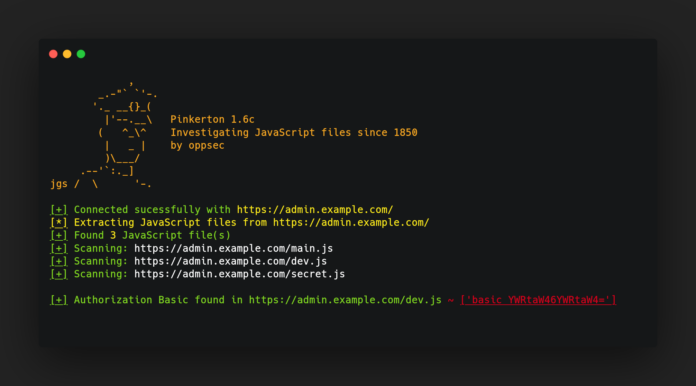
Indonesia, SECRY – Pinkerton Recon Tool – Hello SECRY Readers If you’re a bug hunter or cyber security analyst and diving into the world of web reconnaissance and hunting for hidden JavaScript treasures, you’ve come to the right place.
In this article, we’ll introduce you to Pinkerton, a nifty recon tool designed to seek out and analyze JavaScript files on websites. Pinkerton is your trusty sidekick in the quest for uncovering those gems hidden within the code. So, let’s roll up our sleeves and explore this handy tool that’s been making waves in the world of cyber reconnaissance.
What is Pinkerton?
Pinkerton, available on Github https://github.com/oppsec/Pinkerton, is a versatile reconnaissance tool with the mission of investigating JavaScript files. With 228 stars and 37 forks, it’s gained popularity among cyber enthusiasts looking to dig deeper into website code. Pinkerton is all about unearthing JavaScript treasures, and here’s how it does it:
Key Features
1. JavaScript File Search
Pinkerton’s first superpower is its ability to scan websites or applications and unearth JavaScript files. It’s like having a digital treasure map, but for code.
2. JavaScript File Extraction
Once Pinkerton discovers a JavaScript file, it doesn’t just leave it lying around. It swiftly extracts it from the website or app, ready for further examination.
3. JavaScript File Analysis
Here’s where Pinkerton really shines. It can analyze JavaScript files to uncover sensitive information like basic authorization data, secret variables, and vulnerabilities. Think of it as your cyber detective, sniffing out the juicy details.
Pinkerton Installation : Quick and Easy
Now, let’s get you set up with Pinkerton so you can start your JavaScript reconnaissance journey. Follow these simple steps:
- Clone the Pinkerton repository with this command:
git clone https://github.com/oppsec/pinkerton.gitcd pinkerton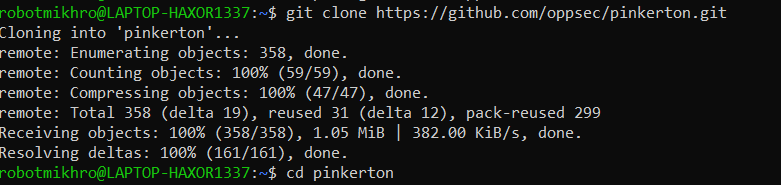
Clone Pinkerton From Github - Install the required libraries with pip3:
pip3 install -r requirements.txt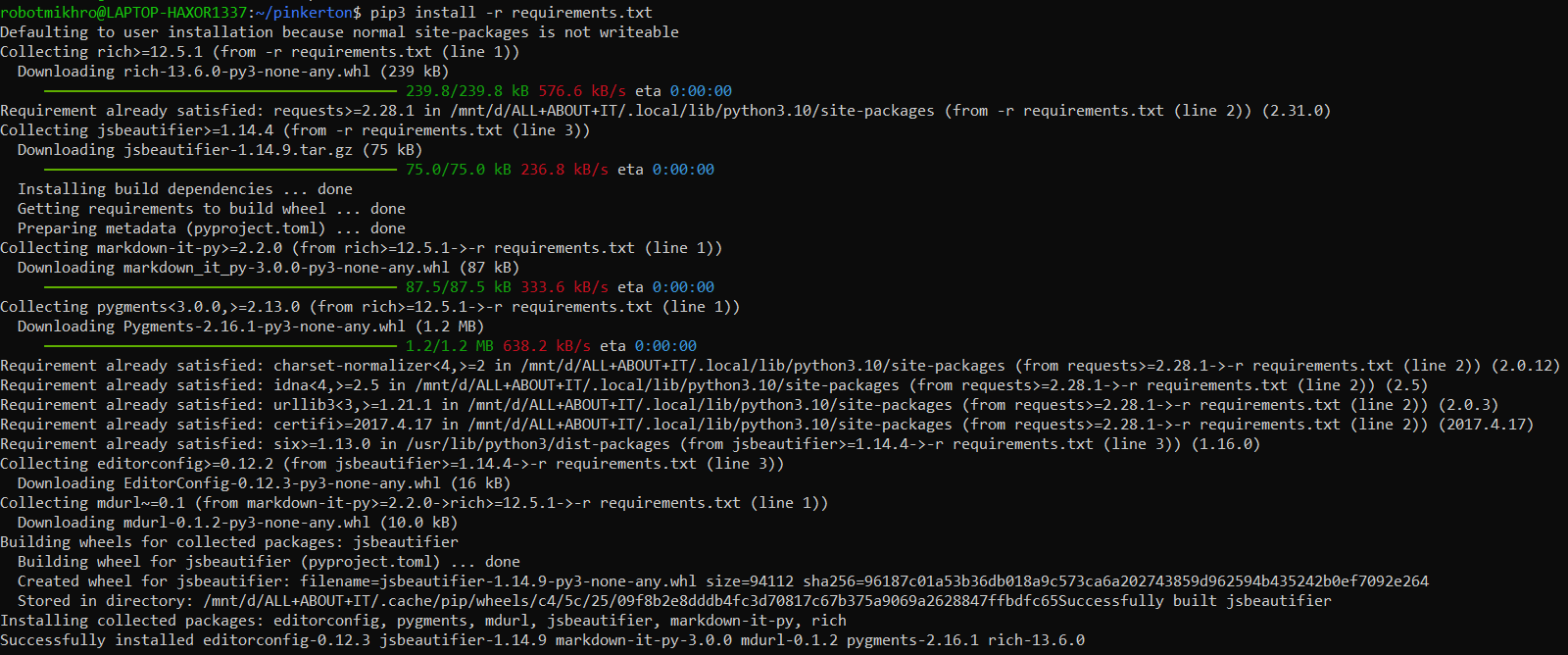
Try Installing PIP requirements for Pinkerton on my WSL - Run Pinkerton by executing this command:
python3 main.py -u https://example.com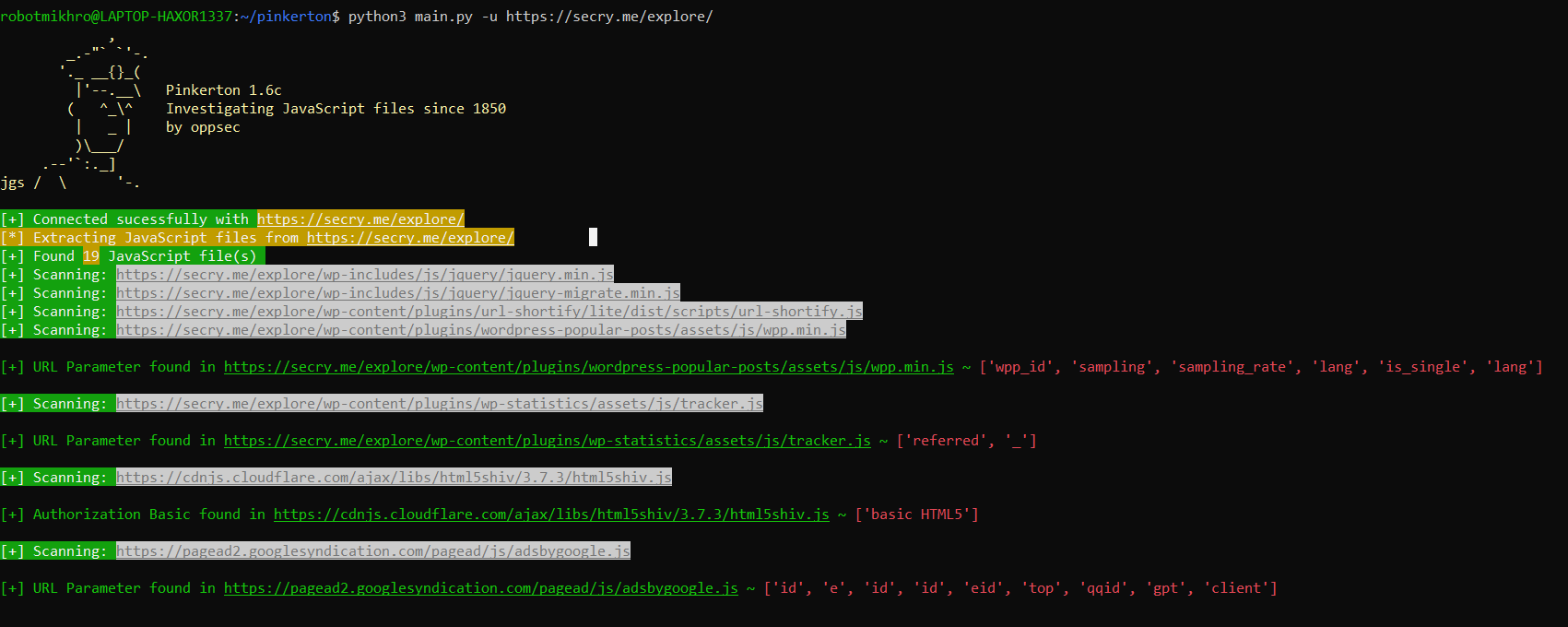
Dockerize Your Recon
Are you a fan of Docker containers? Pinkerton has you covered:
- Clone the repository:
git clone https://github.com/oppsec/pinkerton.git - Build the Docker image:
sudo docker build -t pinkerton:latest - Run the container:
sudo docker run pinkerton:latest
Prerequisites
Before you embark on your Pinkerton adventure, make sure you have Python 3 installed on your machine. You’ll also need to install the required libraries using this command:
pip3 install -r requirements.txt
Credits and Acknowledgments
Pinkerton’s capabilities have been enhanced by the contributions of talented individuals in the cyber community, including:
- m4ll0k (Creator of SecretFinder) for providing regex patterns.
- h33lit (Jubaer Alnazi) for contributing regex patterns.
- zricethezav (Creator of GitLeaks) for sharing regex patterns.
With Pinkerton in your toolkit, you’re well-equipped to embark on your JavaScript reconnaissance missions. So, start scanning, extracting, and analyzing with confidence, and uncover those hidden treasures in the code. Happy recon hunting! 🕵️♂️💻🔍
Just it, thanks for read !