TAG-74 is a Chinese hacker group that has been targeting South Korean organizations for several years. The group has used a variety of techniques to gain access to systems, including phishing emails, malware, and exploiting vulnerabilities in software.
TAG-74‘s primary goal is to steal sensitive data, such as intellectual property, trade secrets, and government information. The group has also been known to launch disruptive attacks, such as denial-of-service attacks.
In a recent report, the security firm FireEye attributed a number of attacks against South Korean organizations to TAG-74. The report found that the group has been targeting a wide range of organizations, including aerospace and defense companies, government agencies, and research institutions.
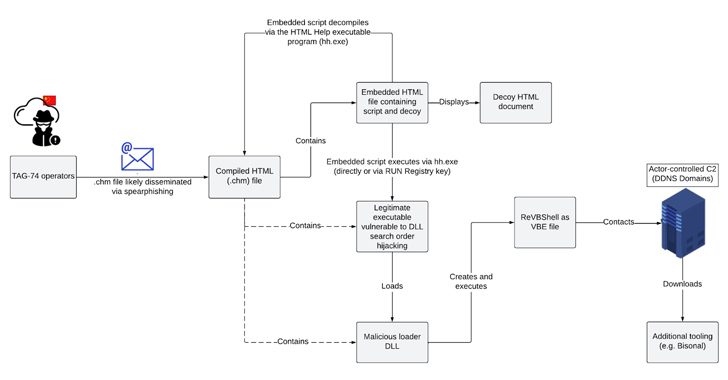
The report also found that TAG-74 has been using a new malware tool called “FASTSOCKET.” FASTSOCKET is a remote access trojan (RAT) that allows attackers to execute commands on infected systems and steal files.
FireEye’s report is a reminder that South Korean organizations are at risk of attack from Chinese hackers. Organizations should take steps to protect themselves by implementing strong security measures, such as:
- Educating employees about cybersecurity best practices. This includes creating strong passwords, being wary of phishing emails, and reporting suspicious activity.
- Keeping all software up to date. This includes operating systems, applications, and security software. Attackers often exploit known vulnerabilities in software to gain access to systems.
- Implementing a layered security approach. This includes using firewalls, intrusion detection systems, and next-generation web application firewalls (NGWAFs) to protect against a wide range of attack vectors.
Organizations should also consider conducting regular security assessments to identify and address any security vulnerabilities before they are exploited by attackers.
Recommendation
In addition to the above recommendations, organizations should also consider the following:
- Having a plan for responding to cyberattacks. This plan should include steps for containing the attack, investigating the incident, and recovering from the attack.
- Working with a reputable security firm. A security firm can help organizations to implement and manage a comprehensive security program.
By following these recommendations, organizations can reduce their risk of being successfully attacked by Chinese hackers.



