JetBrains TeamCity is a popular continuous integration and continuous delivery (CI/CD) platform. Developers use it to automate the software development process, from building and testing code to deploying it to production.
Unauthenticated attackers could exploit a critical security flaw in JetBrains TeamCity, a continuous integration and continuous delivery (CI/CD) software, to achieve remote code execution on affected systems.
The flaw, tracked as CVE-2023-42793, carries a CVSS score of 9.8 and has been addressed in TeamCity version 2023.05.4 following responsible disclosure on September 6, 2023.
If exploited, the vulnerability could allow attackers to steal source code, service secrets, and private keys; take control over attached build agents; and poison build artifacts.
Proof Of Concept?
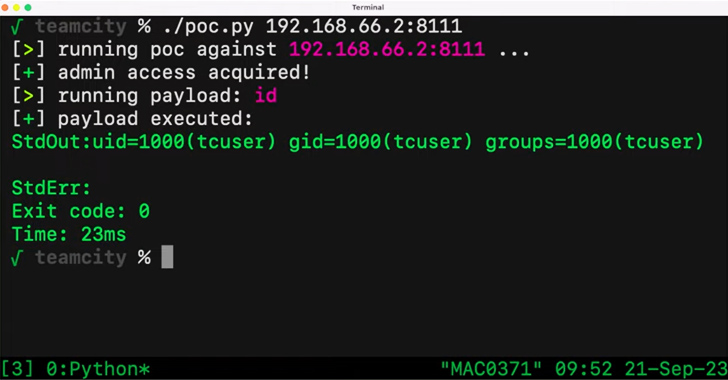
Unauthenticated attackers can exploit CVE-2023-42793 to send specially crafted HTTP requests to JetBrains TeamCity servers. These requests can then allow the execution of arbitrary code on the server, potentially enabling attackers to steal source code, service secrets, and private keys, take control over attached build agents, and poison build artifacts.
JetBrains released a patch for the vulnerability
JetBrains has released a patch for the CVE-2023-42793 vulnerability in TeamCity version 2023.05.4. They also has urged users to upgrade to TeamCity version 2023.05.4 or later as soon as possible to mitigate the risk of exploitation.
While there are no known active exploits of this vulnerability, it is important to note that it is critical to patch all known vulnerabilities as soon as possible. Attackers are constantly looking for new ways to exploit vulnerabilities, and they may develop exploits for known vulnerabilities before patches are released.
Recommendation
In addition to updating TeamCity, users can also take the following steps to protect themselves from this vulnerability:
- Using a layered security approach. This includes using firewalls, intrusion detection systems, and next-generation web application firewalls (NGWAFs) to protect against a wide range of attack vectors.
- Restrict access to TeamCity servers. Only allow authorized users to access TeamCity servers. If possible, use a VPN to connect to TeamCity servers.
- Regularly back up TeamCity data. This will allow you to recover your data if it is compromised by an attacker.
- Use a secure version control system. A secure version control system will help to protect your source code from unauthorized access and modification.
- Use a secure code review process. A secure code review process helps identify and fix security vulnerabilities in your code before deploying it to production.
- Use a secure build pipeline. A secure build pipeline helps protect your build pipeline from attacks and ensures that only trusted code is deployed to production.
- Monitor your build pipeline for suspicious activity. Use monitoring tools to detect and respond to suspicious activity on your build pipeline.
- Educating employees about cybersecurity best practices. This includes creating strong passwords, being wary of phishing emails, and reporting suspicious activity.
- Having a plan for responding to cyberattacks. This plan should include steps for containing the attack, investigating the incident, and recovering from the attack.
By following these steps, users can reduce the risk of this vulnerability exploiting them.



