BLUFFS Attack – CVE-2023-24023 – Researchers at Eurecom have uncovered six new exploits collectively named ‘BLUFFS’, capable of breaching the confidentiality of Bluetooth sessions. Unlike typical attacks dependent on specific hardware or software configurations, BLUFFS exposes two previously unknown architectural flaws in the Bluetooth standard. These vulnerabilities are tracked under the identifier CVE-2023-24023. CVE-2023-24023 affect Bluetooth Core Specification 4.2 through 5.4, raising concerns about the security of billions of devices, including laptops, smartphones, and other common mobile devices.
Understanding BLUFFS: Breaking Bluetooth’s Secrecy
BLUFFS isn’t your typical attack, it comprises exploits aimed at compromising the confidentiality of both past and future Bluetooth sessions. The attack relies on four flaws in the session key derivation process, two of which researchers had not discovered before.
By exploiting these flaws, attackers force the derivation of a short and predictable session key (SKC). Subsequently, the attacker employs brute-force techniques to decrypt historical communications and manipulate future interactions.
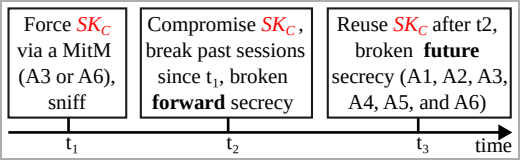
The crux of BLUFFS lies in the attacker’s ability to be within Bluetooth range of two communicating devices. The attacker, posing as one of the devices, manipulates the negotiation process for a weak session key.
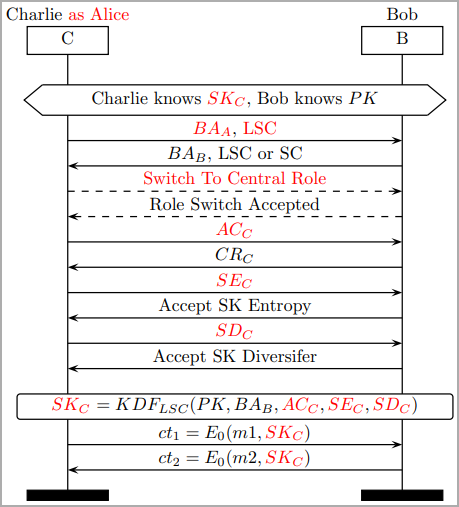
This involves proposing the lowest possible key entropy value and utilizing a constant session key diversifier. The attack is agnostic to whether the victims support Secure Connections (SC) or Legacy Secure Connections (LSC), making it a pervasive threat.
The released paper outlines six BLUFFS attack variations, encompassing different combinations of impersonation and Man-in-the-Middle (MitM) tactics. These strategies remain effective irrespective of the victim’s support for Secure Connections (SC) or Legacy Secure Connections (LSC).
The researchers developed and shared a toolkit on GitHub that demonstrates the effectiveness of BLUFFS. It includes a Python script to test the attacks, the ARM patches, the parser, and the PCAP samples captured during their tests.
Impact and Mitigation Strategies
BLUFFS impacts Bluetooth versions 4.2 through the latest 5.4, affecting devices dating back to December 2014. The researchers tested BLUFFS against various devices running Bluetooth versions 4.1 through 5.2, confirming susceptibility to at least three out of six BLUFFS attacks. The proposed backward-compatible modifications include introducing a new “Key Derivation Function” (KDF) for Legacy Secure Connections (LSC), mutual nonce exchange, and verification, shared pairing keys, enforcing Secure Connections (SC) mode, and maintaining a cache of session key diversifiers to prevent reuse.
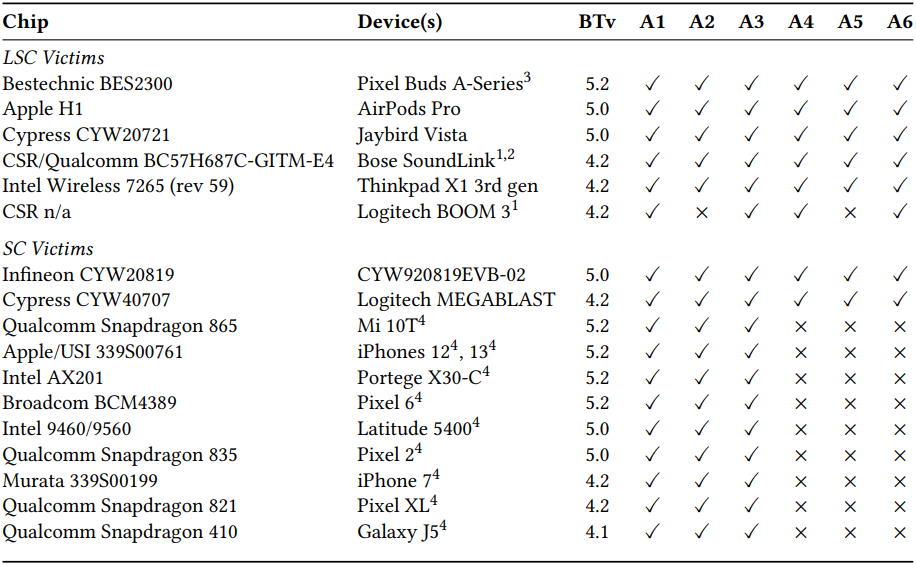
Bluetooth SIG, the organization overseeing Bluetooth standard development, has acknowledged the report from Eurecom and published a statement on its site. In response, they advocate for rejecting connections with low key strengths, employing ‘Security Mode 4 Level 4’ for higher encryption strength, and operating in ‘Secure Connections Only’ mode during pairing. These recommendations aim to bolster session key derivation and mitigate not only BLUFFS but also similar threats, underlining the ongoing efforts to fortify Bluetooth security.



