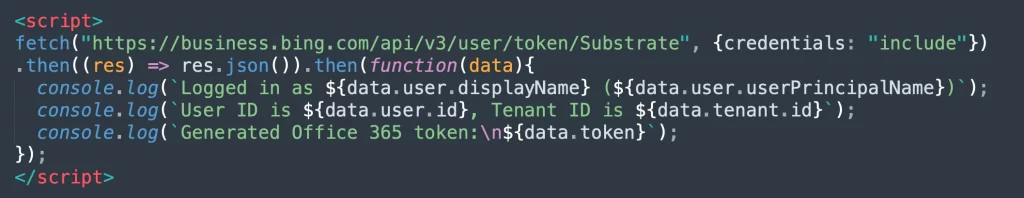
Bing Hacked: Wiz Research, a cybersecurity firm, recently uncovered a significant vulnerability in Azure Active Directory (AAD) that resulted in unauthorized access to multiple Microsoft applications including bing.com hacked.
This misconfiguration in AAD has raised concerns about the security of cloud-based identity providers, particularly with popular services like Azure App Services and Azure Functions. The research conducted by Wiz Research revealed that approximately 25% of multi-tenant applications were vulnerable to this attack vector.
The discovery of this vulnerability has far-reaching implications, as it allowed unauthorized modification of search results on Bing.com, a widely used search engine.
Not only could the attackers manipulate search results, but they could also launch cross-site scripting (XSS) attacks on Bing users, potentially compromising their personal data, including Outlook emails and SharePoint documents.
The Wiz Research team promptly reported their findings to the Microsoft Security Response Center (MSRC), which took immediate action to fix the vulnerable applications.
Microsoft also updated its customer guidance and patched certain AAD functionalities to minimize the risk of further exposure. In recognition of their valuable contribution, Microsoft awarded Wiz Research a bug bounty of $40,000.
A Closer Look at Azure Active Directory (AAD) Misconfigurations
Azure Active Directory (AAD) is Microsoft’s Single Sign-On (SSO) service, commonly used for authentication in Azure App Services and Azure Functions. The misconfigurations in AAD predominantly occur in multi-tenant applications, where the responsibility for validating user identities and implementing appropriate access controls becomes ambiguous.
In the case of Azure App Services and Azure Functions, the lack of clarity regarding validation responsibilities often leads to misconfigurations.
Wiz Research’s scans of the internet revealed that a significant number of multi-tenant apps suffered from authentication bypass vulnerabilities. This indicates a widespread lack of understanding among developers about the importance of validating end-users’ tokens, resulting in these misconfigurations.
The Case Study: Compromising Bing.com Search Result and Office 365 Data
- Part 1 – Reconnaissance:
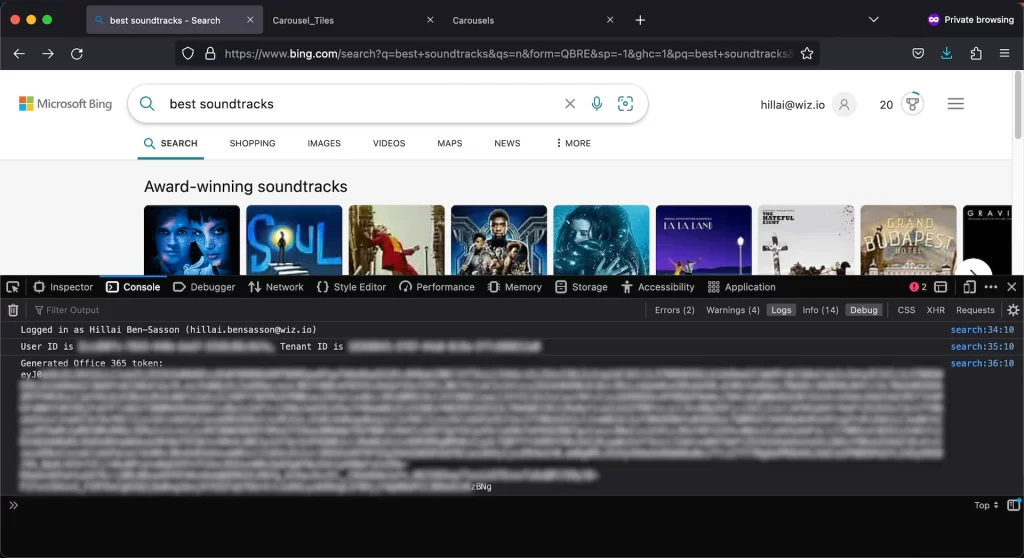
Wiz Research conducted scans on Azure App Services and Azure Functions, ultimately focusing on Microsoft’s own tenant. They discovered the Bing Trivia application (bingtrivia.azurewebsites.net), which allowed unauthorized access. This application served as a content management system (CMS) for Bing.com, enabling the manipulation of search results and launching of XSS attacks. - Part 2 – Altering search results and homepage background:

Change background image of Bing.com Homepage, source: https://www.wiz.io/blog/azure-active-directory-bing-misconfiguration Wiz Research tested their control over Bing’s search results by modifying a carousel section within the CMS, which contained a table featuring search result suggestions displayed on Bing search engine. It also highlighted quizzes and background images that were showcased on the Bing.com homepage on the same day. To their surprise, the changes they have made were immediately reflected on Bing.com. And after confirming their ability to manipulate search results. They promptly reported their findings to Microsoft.
- Part 3 – Attacking Bing users:
Investigating further, Wiz Research discovered that an XSS payload could be used to obtain valid tokens from Bing users, potentially granting access to their Office 365 data. This included Outlook emails, calendars, Teams messages, SharePoint documents, and OneDrive files. The potential impact on millions of users’ sensitive data was significant.
Additional Vulnerable Microsoft Applications
In addition to the Bing Trivia app, Wiz Research identified several other internal Microsoft applications that suffered from similar misconfigurations, putting them at risk of unauthorized access:
- Mag News: A control panel for the MSN Newsletter, enabling the sending of arbitrary emails to a vast audience from a trusted Microsoft email.
- CNS API: An API for Microsoft’s Central Notification Service, allowing the reading and sending of internal notifications to Microsoft developers.
- Contact Center: An API for Microsoft’s Contact Center, managing call center agents for customer representatives.
- PoliCheck: An internal Microsoft application used for political ad verification, which could be manipulated to display false or misleading information.
- MSRC Portal: The Microsoft Security Response Center portal, which handles the reporting and tracking of security vulnerabilities in Microsoft products. Unauthorized access to this portal could have severe consequences, including the ability to exploit undisclosed vulnerabilities.
Following the disclosure of these vulnerabilities, Microsoft has taken immediate action to fix the affected applications and reinforce security measures. They have also conducted internal investigations to identify any unauthorized access and mitigate the potential impact on user data and also rewarded the Wiz Research $40000.
Customer Remediation Guidelines
To ensure the security of Azure Active Directory (AAD) in organizations, it is crucial to address potential vulnerabilities in multi-tenant applications. Administrators can perform a query on AAD service principals and utilize either the Azure Portal or Azure CLI to identify applications that may lack sufficient authorization checks. The recommended remediation actions involve either migrating to single-tenant authentication or implementing claims-based authorization logic tailored to the specific requirements of the application.
The discovery of these misconfigurations serves as a reminder for organizations to prioritize the proper configuration and implementation of security measures when adopting cloud-based identity providers like Azure Active Directory.
Furthermore, it underscores the significance of conducting regular security assessments and vulnerability testing to proactively identify and address any weaknesses in both applications and infrastructure. By adhering to these guidelines, organizations can bolster their overall security posture and safeguard their data effectively.



These are in fact great ideas in regarding blogging.
You have touched some pleasant factors here. Any way keep up wrinting.
Thanks for support us
Hello! I know this is somewhat off topic but I was
wondering if you knew where I could get a captcha plugin for my comment
form? I’m using the same blog platform as yours and I’m having difficulty finding one?
Thanks a lot!
use plugin AIOWP SECURITY
Please let me know if you’re looking for a writer for your
weblog. You have some really good articles and I think I would be a good asset.
If you ever want to take some of the load off,
I’d love to write some material for your blog in exchange for a link back to mine.
Please shoot me an email if interested. Cheers!
thank for your support
Wonderful items from you, man. I have understand your stuff previous to and you’re simply too great.
I really like what you’ve acquired here, certainly like what you are saying and the way
wherein you say it. You are making it enjoyable and
you still take care of to stay it smart. I can’t wait to
read much more from you. This is really a tremendous site.
Nice blog here! Also your website a lot up fast! What host are you the use of?
Can I am getting your affiliate link to your host?
I desire my website loaded up as fast as yours lol
Thanks in favor of sharing such a nice idea, article is fastidious, thats why i have read it fully