Indonesia, SECRY – Welcome to the world of web application security! In 2023, as technology continues to advance, so do the risks that come along with it. In this article, we will delve into the latest edition of the OWASP Top Ten, your trusty guide to understanding and mitigating the most critical security threats faced by web applications today.
What is OWASP Top Ten
The OWASP Top 10 is your go-to, tried-and-true companion of web application security. It serves as an essential reference point for developers and security professionals, shedding light on the ever-evolving landscape of security threats. Updated every two to three years, the OWASP Top Ten ensures you’re equipped to tackle the latest trends and vulnerabilities head-on.
The OWASP Top 10 in 2023, Still Same
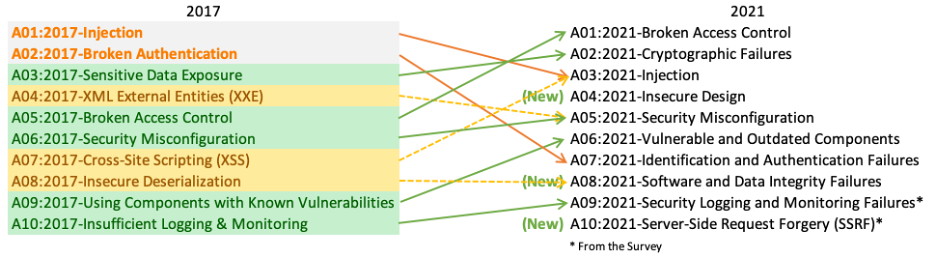
- Broken Access Control
Picture this: an intruder gaining unauthorized access to your web application. How? Through a web of misconfigurations, stolen credentials, or cleverly bypassed authentication methods. Broken Access Control is a lurking danger that can’t be underestimated. - Cryptographic Failures
Cryptographic jargon can be daunting, but mishandling cryptographic algorithms or implementations can result in intercepted or tampered data. Your data’s security, both in transit and at rest, hinges on correctly wielding cryptography. - Injection
When untrustworthy data infiltrates your application, be it through user input or parameters, you’ve got yourself an Injection vulnerability. Attackers could seize the opportunity to execute their malicious code or access data they shouldn’t. - Insecure Design
Security should be a part of your application’s DNA from the get-go. Neglecting security in your design can lead to vulnerabilities such as weak authentication, shoddy data storage practices, and inadequate logging and monitoring. - Security Misconfiguration
A well-configured application is your first line of defense. Avoid using default passwords, unnecessary features, and failing to apply security patches. Security Misconfiguration is an Achilles’ heel that attackers won’t hesitate to exploit. - Vulnerable and Outdated Components
If your application relies on outdated or vulnerable components, it’s akin to leaving your front door wide open. Attackers are lurking, ready to pounce on those known vulnerabilities. - Identification and Authentication Failures
When your application falters in user authentication, attackers may gain unauthorized access to accounts or systems. Getting user identification and authentication right is crucial. - Software and Data Integrity Failures
Protecting the integrity of your software and data is paramount. Failures in this area could lead to data manipulation, deletion, or even malicious code injection. Stay vigilant! - Insufficient Logging and Monitoring
Imagine not having a security camera when a burglary occurs. Insufficient Logging and Monitoring leaves you blind to malicious activities, making detection and response a formidable challenge. - Server-Side Request Forgery (SSRF)
Tricking your web application into making unintended requests to remote servers—this is what Server-Side Request Forgery (SSRF) entails. It’s a cunning method attackers can use to access sensitive data or launch assaults on other systems.
Beyond the OWASP Top 10
While the OWASP Top 10 is your trusty guide, it’s essential to remember that it doesn’t cover every possible security risk. There’s a broader landscape out there, and you should remain vigilant against threats like:
- Denial-of-service attacks
- Session hijacking
- Phishing attacks
- Man-in-the-middle attacks
- SQL injection attacks
- Cross-site request forgery (CSRF) attacks
- Directory traversal attacks
- File inclusion attacks
- Remote code execution attacks
These additional risks are equally important to understand and defend against to ensure comprehensive security for your web applications.
Conclusion
In the dynamic world of web application security, staying informed and prepared is the key to success. The OWASP Top Ten is your steadfast companion, but remember, it’s not a one-size-fits-all solution. Consult with security experts, keep your knowledge up-to-date, and always prioritize the safety of your web applications. With these steps, you can confidently navigate the ever-evolving cyber landscape in 2023 and beyond.
Reference:
- https://devsday.ru/blog/details/22099
- https://owasp.org/www-project-top-ten/



