Overview
A critical vulnerability has been discovered in the WooCommerce Payments plugin, which is installed on over 500,000 WordPress websites. The vulnerability, if not resolved, could allow unauthorized attackers to gain administrative access to impacted stores.
This would enable an unauthenticated attacker to impersonate an administrator and take over a website without any user interaction or social engineering required.
The company has released patches for the affected versions and urges users to update their plugins immediately.
The Vulnerability
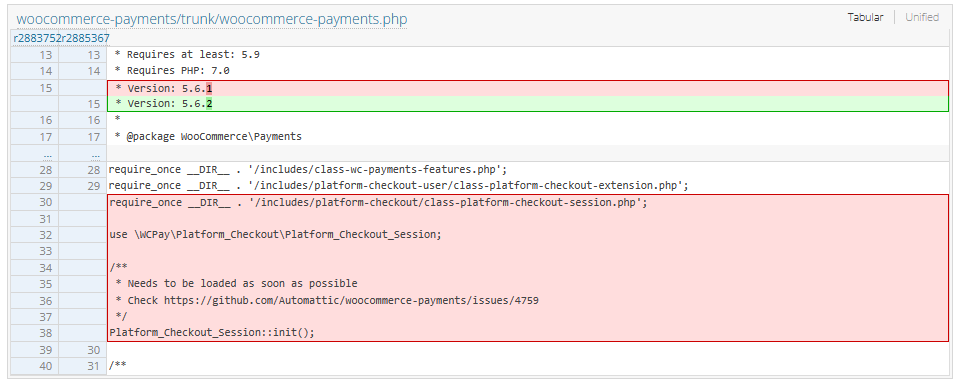
This security flaw, could enable an attacker to gain unauthorized admin access to impacted stores without any user interaction or social engineering required. The vulnerability affects versions 4.8.0 through 5.6.1 of the WooCommerce Payments plugin.
The issue lies in a PHP file called “class-platform-checkout-session.php.” Michael Mazzolini of Swiss penetration testing company GoldNetwork is credited with discovering and reporting the vulnerability.
Recommended Actions
Website administrators using the affected plugin should take the following actions:
- Update WooCommerce Payments to version 5.6.2 immediately.
- Change all administrator passwords.
- Rotate payment gateway and WooCommerce API keys.
- Check for newly added admin users and unfamiliar IP addresses.
While it is unlikely that passwords themselves were compromised, it is advised to change them if they are reused across multiple websites. Additionally, changing the salts within the wp-config.php file can provide extra security.
WooCommerce’s Response
WooCommerce worked with WordPress to auto-update sites using affected versions of the software. Patched versions include 4.8.2, 4.9.1, 5.0.4, 5.1.3, 5.2.2, 5.3.1, 5.4.1, 5.5.2, and 5.6.2.
Source: https://blog.sucuri.net/
The maintainers of the e-commerce plugin have also disabled the WooPay beta program due to concerns that the security defect could impact the payment checkout service.
Potential Exploits
While there is currently no evidence of the vulnerability being actively exploited, it is expected to be weaponized on a large scale once a proof-of-concept becomes available. Wordfence researcher Ram Gall cautioned that mass exploitation targeting this vulnerability is likely in the near future.
Protection Measures
Wordfence has released a firewall rule on March 23, 2023, to protect sites with Wordfence Premium, Wordfence Care, or Wordfence Response installed. If your site is running the free version of Wordfence, the rule will become available on April 22, 2023.
It is highly recommended that you forward this advisory to any friends or colleagues using the WooCommerce Payments plugin on their websites. Raising awareness within the WordPress community is crucial for ensuring the security of affected sites.
Incident Response Services
If you believe your site has been compromised as a result of this vulnerability or any other issue, Wordfence Care offers Incident Response services. For immediate site cleaning, Wordfence Response provides the same service with 24/7/365 availability and a 1-hour response time. Both products include hands-on support in case you need further assistance.Privilege Escalation.
Final Thoughts
The critical vulnerability found in the WooCommerce Payments plugin underscores the need to keep plugins updated and enable automatic updates.
WooCommerce’s security team swiftly addressed the issue, making it vital for website administrators to act immediately to safeguard their sites from potential exploits.
Currently, no evidence suggests active exploitation of this vulnerability. However, Wordfence researcher Ram Gall cautions that large-scale weaponization could occur once a proof-of-concept becomes available.



