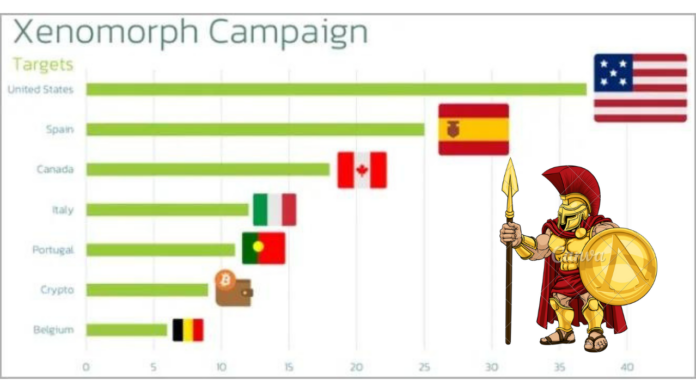
Security researchers have discovered a new variant of the Xenomorph banking trojan that is targeting over 35 financial institutions in the United States. The new variant, which was first observed in September 2023, is more sophisticated than previous versions of the Xenomorph trojan and is more difficult to detect.
Xenomorph is a type of malware that steals sensitive financial information from victims, such as login credentials, credit card numbers, and Social Security numbers. The trojan can be installed on devices through phishing attacks or by exploiting vulnerabilities in software and hardware.
Once installed, Xenomorph can monitor a victim’s online activity and steal their financial information when they log into their bank accounts or other financial websites. The trojan can also steal data from mobile devices, such as smartphones and tablets.
The new variant of Xenomorph is particularly dangerous because it is able to bypass many traditional security measures, such as antivirus software and sandboxing. The trojan also uses a variety of techniques to evade detection, such as obfuscating its code and using encryption.
Security researchers are still learning about the new variant of Xenomorph, but they have identified a few key features:
- The trojan is able to target a wider range of financial institutions than previous versions of Xenomorph.
- The trojan is more difficult to detect and remove than previous versions of Xenomorph.
- The trojan uses a variety of techniques to steal financial information from victims, including keylogging, screen scraping, and form grabbing.
More Detail about Xenomorph
In addition to the above, here are some other details about the new variant of Xenomorph:
- Xenomorph made its initial appearance in the wild during the early months of 2022, functioning as a banking trojan with a focus on 56 European banks, utilizing screen overlay phishing tactics. Its distribution occurred through the Google Play platform, amassing a staggering 50,000-plus installations.
- The trojan is able to steal two-factor authentication (2FA) codes from victims. 2FA is a securitymeasure that requires users to enter a code from their phone in addition to their password when logging into their accounts. This makes it more difficult for attackers to gain access to accounts, even if they have the victim’s password.
- The trojan is able to inject malicious code into legitimate websites. This allows the trojan to steal financial information from victims when they visit these websites.
- The trojan is able to spread through networks. Once the trojan is installed on one device on a network, it can spread to other devices on the network.
New Variant and New Campaign
In the most recent campaign, the malware operators have chosen to employ phishing pages, enticing visitors to update their Chrome browser and deceiving them into downloading the malicious APK.

While the malware still relies on overlays for data theft, it has broadened its range of targets to encompass financial institutions in the United States and several cryptocurrency applications.
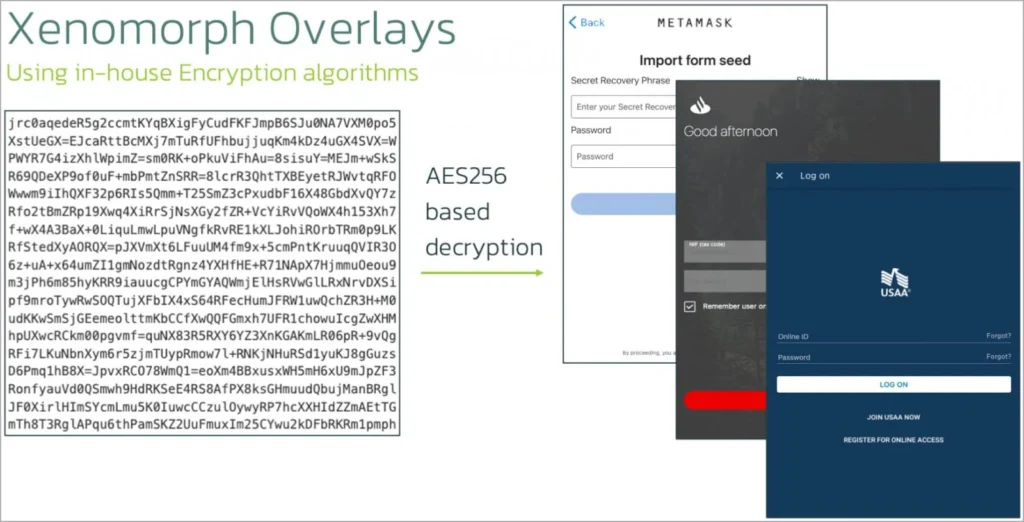
How to Protect?
Organizations can protect themselves from the new variant of Xenomorph by taking the following steps:
- Implement multi-factor authentication for all remote access and privileged accounts.
- Segment your network to prevent attackers from moving laterally if they do gain access.
- Regularly back up your data and store the backups offline.
- Educate your employees about cybersecurity best practices, such as phishing awareness and password security.
- Keep your software and hardware up to date with the latest security patches.
- Use a web application firewall (WAF) to protect your websites from malicious traffic.
- Deploy a network intrusion detection system/prevention system (IDS/IPS) to monitor your network for suspicious activity.
If you believe that your organization has been targeted by the new variant of Xenomorph, you should immediately contact a cybersecurity professional for assistance.
Additional information
- The new variant of Xenomorph is believed to be distributed through phishing attacks. Phishing attacks are emails or websites that are designed to trick victims into revealing their personal information or clicking on malicious links.
- If you receive an email or visit a website that claims to be from a financial institution, but something looks suspicious, do not click on any links or enter any personal information. Instead, contact the financial institution directly to verify the email or website.
- Security researchers are also advising users to be wary of downloading apps from unofficial app stores. Malicious apps can be disguised as legitimate apps and can be used to install malware on devices.
- If you need to download an app, only download it from the official app store for your device.
Users should also be careful about what information they share online. Avoid sharing personal information on social media or other public websites.